Built on a privacy-first architecture
Security-first design and radical transparency form the cornerstone of our approach to technology development. From rigorous security controls to full traceability of every transformation, we ensure your data is not just protected but auditable.

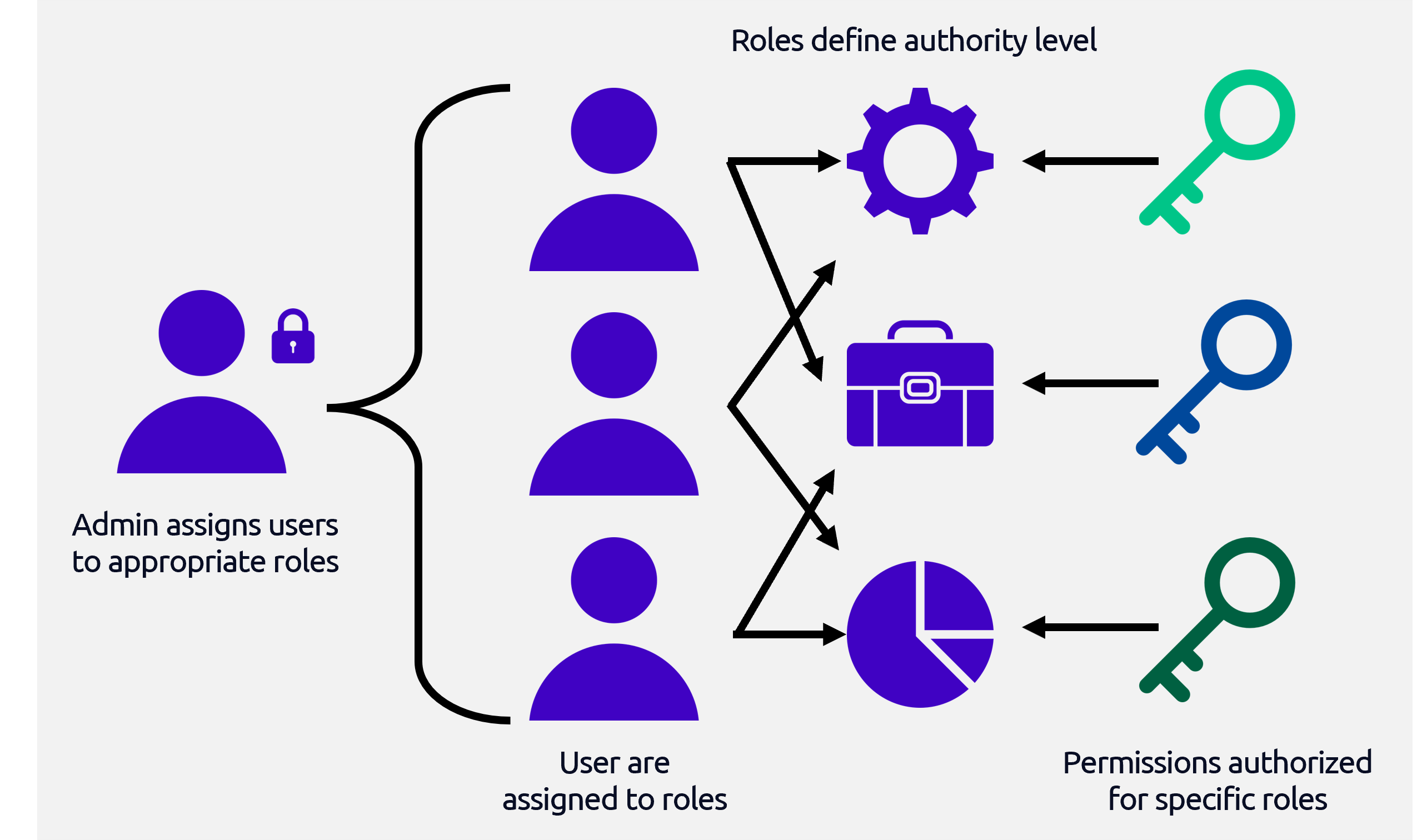
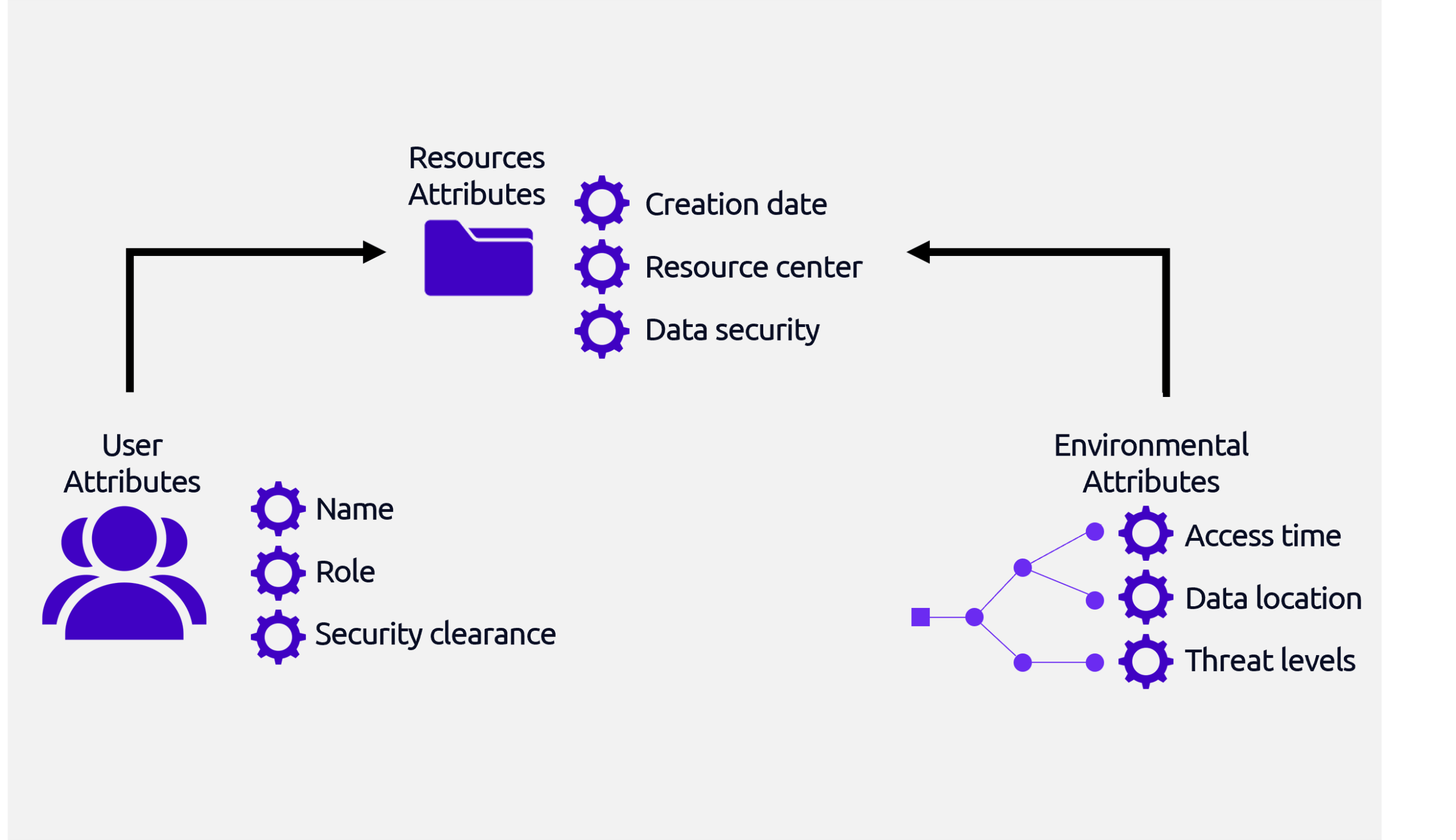
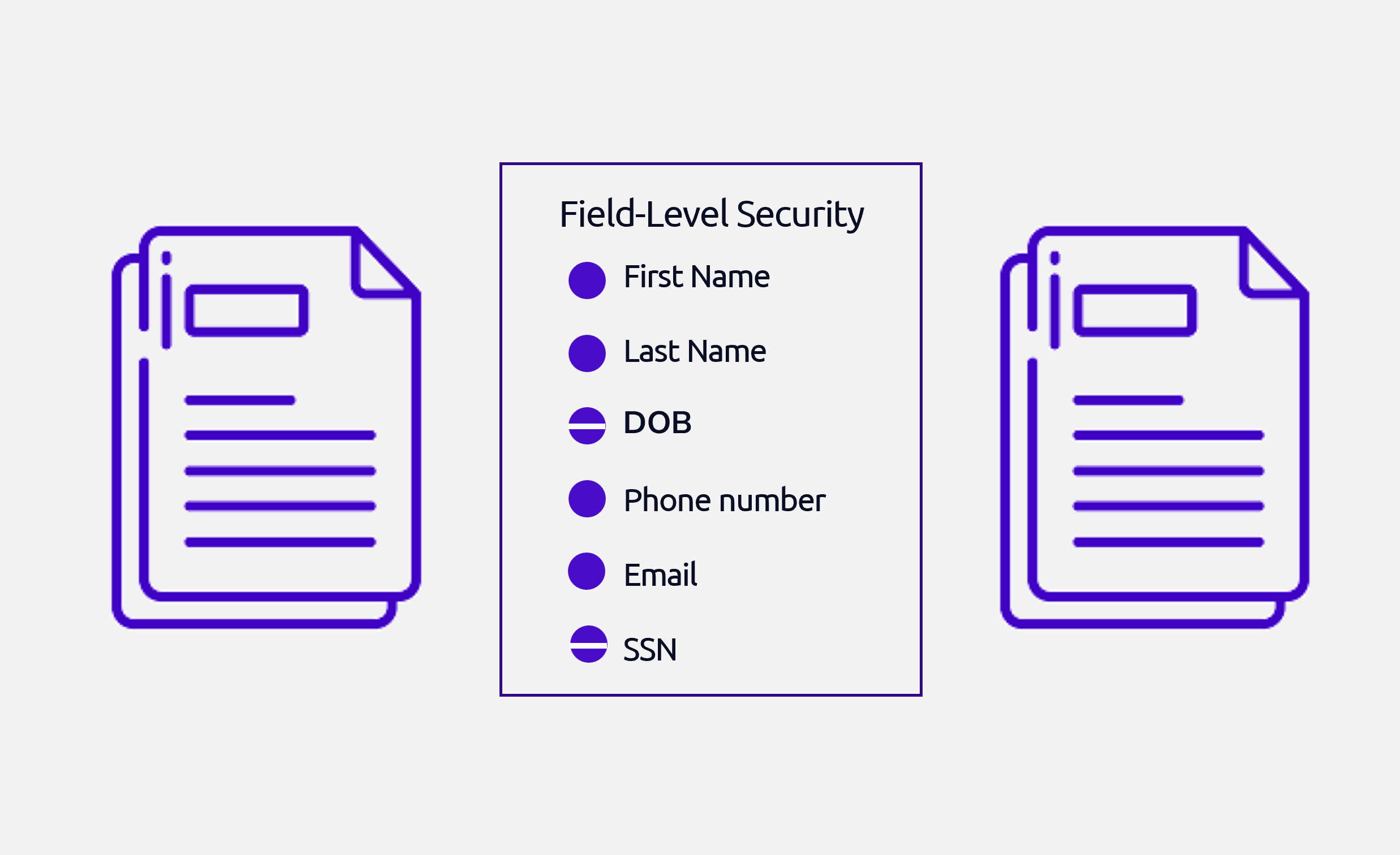
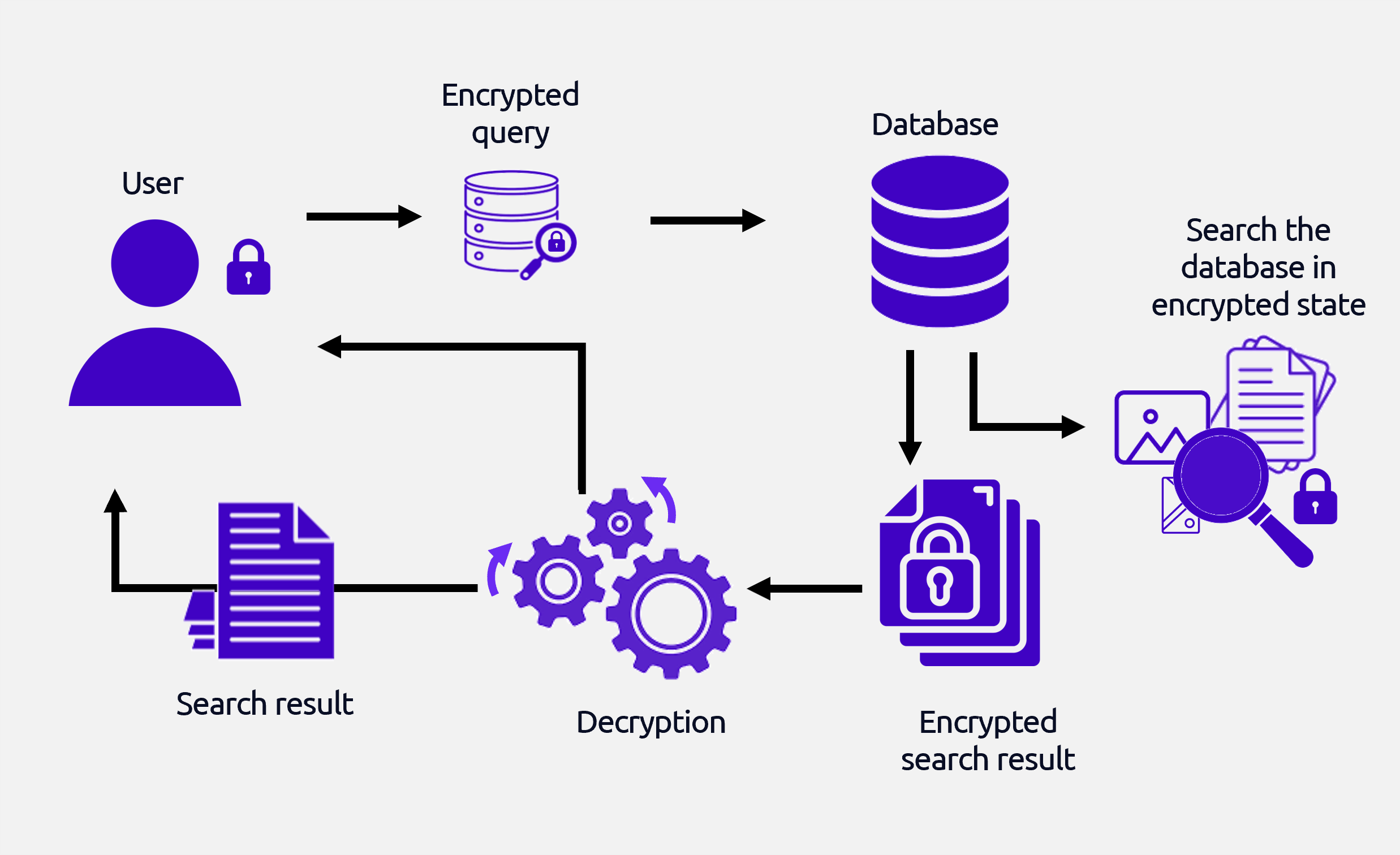
Zero-Trust Architecture Benefits
Zero trust ensures that data and models remain protected at
all times.

Responsible AI Through Privacy-Preserving Collaboration
Axonis embraces responsible AI by:
- Detecting bias across distributed datasets without centralizing data
- Enabling explainable AI through collaborative transparency methods
- Supporting continuous post-deployment monitoring via decentralized evaluation
- Implementing robust privacy protection by keeping data local
- Ensuring compliance with industry standards for ethical AI development
Talk to an expert!
We’d love to tell, or show, you more about our zero-trust approach.